
Applicant tracking systems process critical and confidential information every day. Social Security numbers, bank details, employment history, and background check results are all valuable intel for cyber criminals. This data poses a serious risk to any organization that fails to keep it secure.
As companies use more AI, automation, and third-party tools in hiring, the risk of security breaches increases. HR leaders must ensure that their software vendors treat data security as a core function, not an afterthought.
At Fountain, we build security into every aspect of our platform. In this post, we break down the top security practices every HR tech platform should follow and explain how we use them at Fountain.
1. Security and Compliance Must Be Verified, Not Assumed
Any vendor can claim to be secure. The real question is whether they have the independent certifications and testing to prove it.
What to look for:
- SOC 2 Type II attestation, which verifies ongoing security controls over time
- ISO 27001 certification, the global gold standard for information security
- Compliance with GDPR, CCPA, and other privacy regulations
✅ At Fountain:
Independent auditors have certified Fountain in SOC 2 Type II and ISO 27001:2022. We stay fully compliant with GDPR, CCPA, and other global standards. We conduct annual audits and penetration tests, respond to risks based on their severity, and keep our security status available at all times.

2. Security-Focused Access Controls Are Essential
Poor access controls are among the most common causes of data exposure. Systems should support flexible, granular permissions and require multiple layers of verification.
What to look for:
- Role-based access control (RBAC)
- Single sign-on (SSO) with SAML 2.0
- Mandatory multi-factor authentication (MFA)
- VPN enforcement for internal access
✅ At Fountain:
We enforce MFA and VPN access across all environments, support SAML-based SSO, and allow customers to assign roles or create custom permission sets.

3. Data Security Requires End-to-End Encryption
Teams must encrypt data while it moves through networks and systems, not only when storing it.
What to look for:
- AES-256 encryption at rest
- TLS 1.2+ encryption in transit
- Secure key management with automatic rotation
✅ At Fountain:
All applicant and customer data is encrypted using AES-256 while stored and secured using TLS protocols during transmission. Our internal key management system manages and rotates encryption keys according to industry best practices.

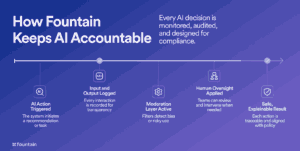
4. AI Must Be Governed by Guardrails, Not Guesswork
As AI becomes more common in hiring platforms, it is important to control the risks. Organizations should manage this through strong policies, ongoing monitoring, and built-in audit systems.
What to look for:
- Audit trails for all AI actions
- Moderation layers to detect bias or harmful content
- Clear internal usage guidelines and oversight
✅ At Fountain:
The system logs every AI action along with its inputs, outputs, and metadata to ensure full transparency. We have a live moderation layer that flags potential risks such as prompt injection or misuse. A dedicated AI governance board sets and enforces internal policies.
5. Security Culture Starts With People
Technology alone cannot secure a system. Leaders must train employees, enforce processes, and maintain strong internal accountability.
What to look for:
- Background checks for employees with data access
- Confidentiality agreements and security onboarding
- Regular phishing simulations and mandatory security training
✅ At Fountain:
All employees with access to sensitive data undergo background checks and receive security onboarding on day one. We run annual training programs and simulate phishing attacks to reinforce awareness. An anonymous reporting line allows employees to flag risks early.

6. System Availability Is a Security Issue Too
Outages and degraded performance can interrupt hiring, lead to missed candidates, and increase security risks. Teams must design the infrastructure to be resilient.
What to look for:
- 99.99% uptime guarantees
- Active-active failover systems
- Annual disaster recovery drills
✅ At Fountain:
Our team builds systems that grow easily and stay reliable worldwide. We keep a 99.99% uptime guarantee and live disaster recovery drills every quarter to ensure we can restore service and protect data within an hour if needed.

Final Thought: Trust Starts with Security
Security is not optional. As hiring becomes more digital, more AI-driven, and more distributed, the risks continue to grow. The cost of failing to address them also continues to rise.
HR leaders must evaluate solutions based on trust, accountability, and long-term security, not just feature sets.
At Fountain, we protect applicant and employer data with the same care and urgency we expect for our own. In today’s hiring landscape, trust is not automatic. We earn it through every decision we make, every safeguard we implement, and every standard we uphold.


